Employee turnover is a fact of life. When an employee leaves, there are cybersecurity measures we recommend following. Whether the separation with the departing employee was amiable or not, it is best to ensure the safety of your company data.
In fact, up to 25% of the data a precious employee can access is sensitive data. Having a process in place can prevent accidental or planned data breaches. Use these best practices to maintain cybersecurity in your company after an employee leaves:
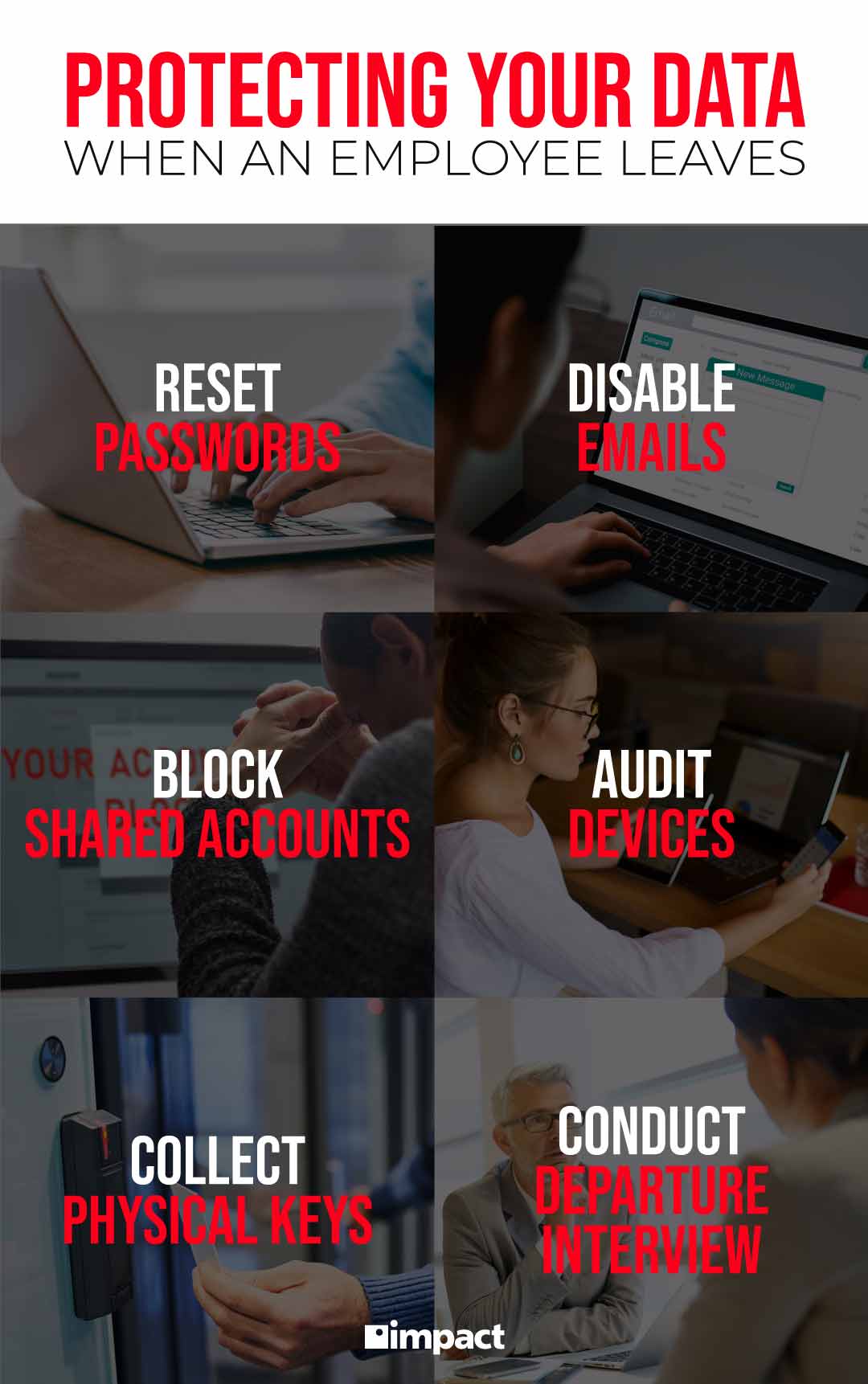
Reset Passwords
The first step to prevent data breaches is to disable a departing employee’s password. Blocking their user sign-in can take some time, which is why disabling their password will set up the first line of defense. A manager with an admin account can change the password until you can disable the user login later.
You can generate a password or change it to anything, as long as access is revoked when the employee leaves. This way, any company data or networks are protected from being tampered with or deleted.
Don’t forget to remove any password recovery option too, so that the departing employee cannot use another device or email address to access their changed password.
Disable Company Emails
After changing passwords, disable any company emails when your employee leaves. The company email is most likely the key they use to access not only company communications, but also shared clouds or shared app accounts. By disabling their email, you are making sure that they cannot log in to all of the accounts where private project data may be stored.
Numerous cyberattacks are attributed to unauthorized email use. Blocking access prevents any ex-employee from engaging in phishing scams or malware uploads. You can also consider implementing an email protection solution, which can use filters and threat management as another layer to safeguard your company.
Block Access to Shared Accounts
About 40% of former employees have logged into a company account after parting ways with an employer. Shared accounts within the company do facilitate project completion while team members work together. When a team member leaves, however, to avoid risks or time-consuming setup of new accounts, it’s best to block a departing employee’s access.
Shared accounts may include project calendars, cloud services, messaging apps, etc. To protect yourself from any data breaches, it’s best to have an inventory of these accounts and immediately change passwords when an employee leaves.
One way to achieve this is by ensuring your IT team can monitor suspicious activities, so that other teams don’t have to worry about data losses.
Related: Impact Network Control: Remote Monitoring and Management (RMM)