New phishing technique uses Microsoft program to attack organizations, even if they don’t use it
Microsoft Office Sway has found itself at the center of a new phishing concern.
Over the last few years, phishing attacks have become the primary tool at the disposal of cybercriminals.
In fact, phishing accounts for a staggering 90% of all data breaches.
Falling victim to such an attack can be disastrous (and often fatal) to a business.
The average financial cost of a data breach is $3.86m
Related Post: Why a Disaster Recovery Plan Is Vital for SMBs
With cyberattacks increasing on small and midsize businesses—43% of all attacks target SMBs—decision makers and owners are understandably concerned about the state of cybersecurity.
Hackers dedicate their time to coming up with new ways to hoodwink unsuspecting victims.
Particularly worrying for business owners is the success rate of these attacks.
30% of phishing messages are opened by targeted users, and 12% of those will click on the malicious attachment or link in the email.
Hackers now have a new favorite tool: Microsoft Sway.
What Is Microsoft Sway?
Microsoft Sway is one of the latest products in the company’s efforts to invest more heavily in its cloud-only services.
Released in 2015, Sway essentially acts as the web and mobile version of PowerPoint.
Where PowerPoint is older, clunky, and heavier; Sway is lean, slick, and geared toward being lightweight and easy to use.
It allows users to create presentations and newsletters and gives them a landing page for their Sway.
Why Are Hackers Using Microsoft Sway for Phishing?
For cybercriminals, authenticity is key.
Rudimentary phishing emails, with spelling and grammar errors, pixelated logos, and suspicious email addresses are far more likely to be found out by users than more sophisticated efforts.
With Sway, they are given a landing page, which presents itself as an authentic and legitimate webpage that can easily fool unsuspecting victims.
There are characteristics that make Sway an ideal tool for criminals, namely:
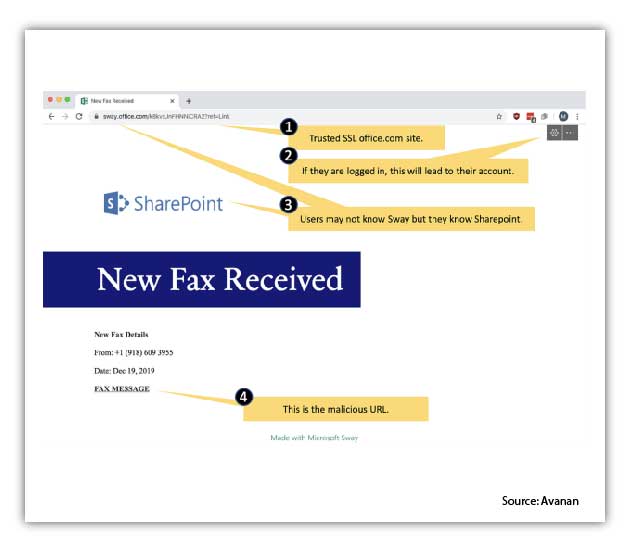
- Sway pages are hosted on the office.com domain, giving it a crucial stamp of approval that allows it to be “trusted” by Microsoft
- If you are logged into your Office account, Sway pages are stylized with Office 365 branding that makes it appear even more legitimate
- Familiar branding, such as the SharePoint logo, between first contact and to finish adds another level of authenticity to these scams
Take a look at the following, would you be able to tell this was malicious?
How Does It Work?
Hackers utilize phishing with Microsoft Sway in much the same way a traditional phishing campaign works.
Related Post: Infographic: Top 13 Phishing Stats SMBs Should Know
You’ll receive an email, which will likely come from a domain that is associated with Microsoft, like example.onmicrosoft.com.
Because Microsoft trusts Sway and Office domains, these addresses will often get through strict email filters and straight into your inbox.
76% of businesses reported being a victim of a phishing attack in the last year
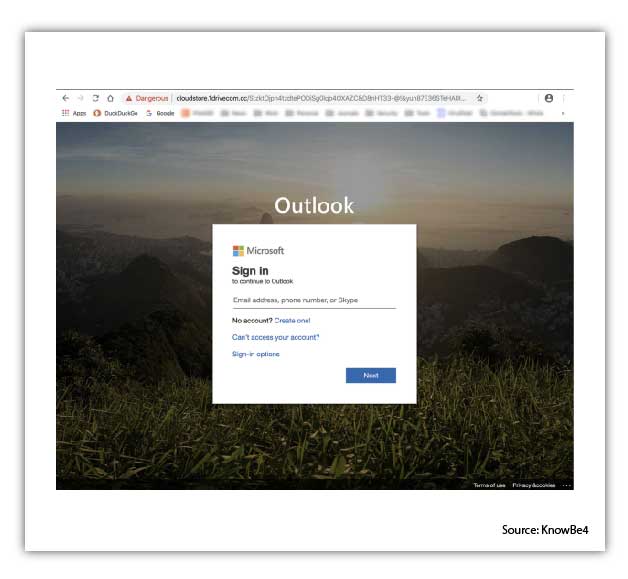
Once you click through on the email, it directs you to a landing page—that page will often look like the familiar login screen for Office 365.
Then when you have entered your credentials into the username and password form boxes, they have access to your account.
You can be vulnerable to these attacks even if you don’t use Sway.
The only thing you need for them to attack is an email address for them to send a message to.
Notice how convincing the following login screen is:
Why Are They Successful?
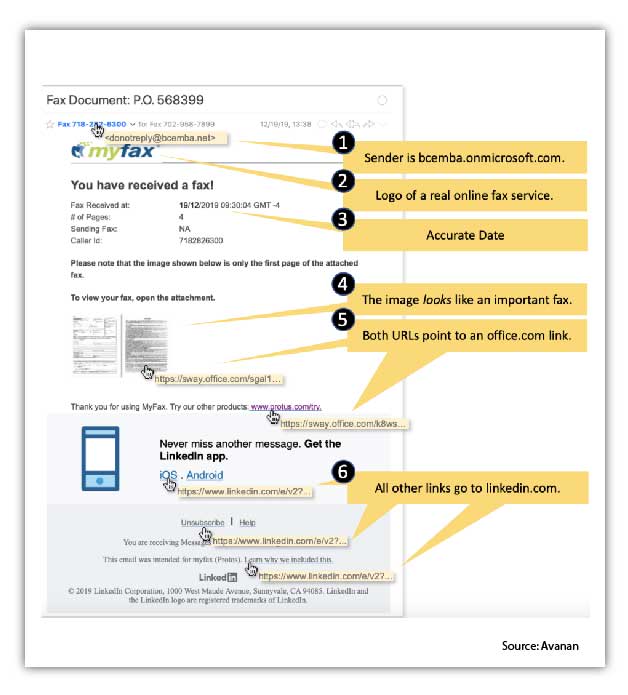
While attackers have been using Sway in their attacks for a while, the most common emerging threat is sending supposed voicemail or even fax alerts to users.
Like any well-orchestrated phishing attack, it plays on your curiosity, as you’re left wondering who called you and why.
Many phishing campaigns are easy to spot by users because they are littered with giveaways that alert suspicion.
These new campaigns are different, maximizing authenticity and minimizing anything that might reveal its true nature.
Since these attacks are something of a zero-day phenomenon, there are little protections out there.
Given the prevalence of these threats, it is likely that cybercriminals will also use other platforms, like Google’s G-Suite, to perform attacks in the future.
Example of a suspicious email regarding a fax received:
Microsoft’s Response to Phishing Concerns
In response to the swathe of phishing attacks, Microsoft commented on their filtering to TechRepublic:
“Contrary to marketing claims, Microsoft does not automatically trust any domain, including the Office and Sway domains. All links are analyzed, assessed and compared to known attack vectors, including local domains. Additionally, Microsoft performs a complete assessment of Sway content, including the scanning of links on the pages.”
It’s worth noting, that in spite of Microsoft’s response, several of these kinds of attacks have indeed bypassed Microsoft’s email filtering, and have found success by specifically using Office and Sway domains because they are not being blocked.
How to Stay Protected
Users who are targeted in these attacks almost always receive the same message about a voicemail or fax.
Blacklisting senders is a game of whack-a-mole, as cybercriminals use many multiples of senders and addresses.
Many are instead blacklisting sway.office.com in their filters until the phishing issue is fully fixed by Microsoft.
Until that time arrives, the best advice is to do the same and educate employees to protect yourself as best as possible.
Cybersecurity attacks lead to data breaches, which are extremely expensive to organizations, and in many cases, cost them their business.
At Impact, our carefully vetted cybersecurity program offers best-in-class tech solutions and education for employees to give you the very best security a company can have. For more information, take a look at our Managed Cybersecurity service and learn about how we can keep your business safe from cyberattacks. Click here!